At WWDC this year, Apple introduced several changes related to identity that raised some confusion regarding how macOS and Jamf Connect will work together going forward. We would like to clear this up and help our customers better understand how macOS Catalina with Jamf Connect can provide the best possible Apple experience for users.
Apple announced several new features that will be available with macOS Catalina in October:
- Customized Enrollment, enabling a mobile device management (MDM) server to specify an authentication web page to load during initial configuration with either Apple Business Manager or Apple School Manager
- Managed Apple IDs for Business (with support for Federation through Microsoft Azure AD), enabling the use of Apple services like iCloud Drive and Notes using one set of existing credentials
- A framework for Single Sign-On app extensions that will enable employees to seamlessly log in to websites and apps, if their cloud identity provider has built a supported app
- The inclusion of a first-party extension to support Kerberos authentication and password syncing to a local account
Although Customized Enrollment can show any type of authentication during initial configuration, verifying that user is allowed to complete set up of the Mac, macOS does not enforce the user to use the same password as their identity provider (IdP). This means that out of the gate, macOS authenticates a username, but now the user has two passwords. And although many companies will take advantage of the first-party extension to support on-premises Active Directory and Kerberos, most customers are moving towards cloud identity providers for additional security and seamless integration with cloud-based apps.
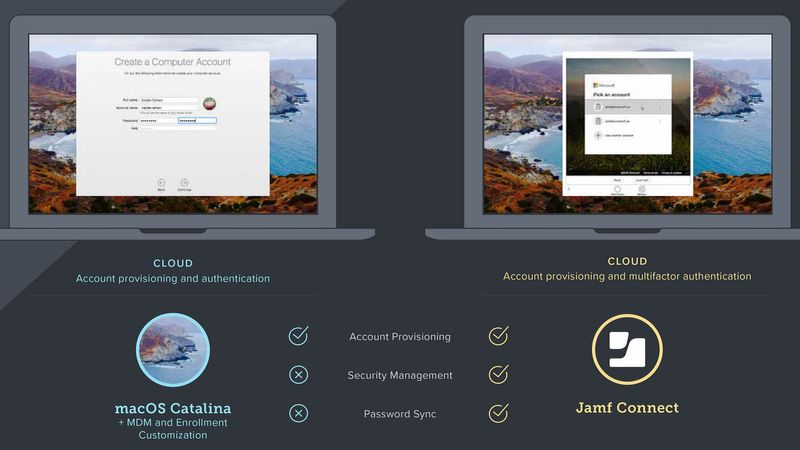
For organizations that use a cloud identity provider and want to enforce a single set of credentials across the entire experience, Jamf Connect takes the value of account provisioning one step further. Jamf Connect gives IT and users the benefit of a consistent username and password during provisioning, plus security management capabilities after provisioning. The following are the benefits customers will gain with Jamf Connect:
Account Provisioning
- Improved user experience with synchronized cloud identity and Mac account credentials
- Each user has a single set of credentials, resulting in an organized fleet of Macs for IT to manage
- Required login via identity provider, allowing for multifactor authentication with each login
Security Management
- Ability to track and monitor what devices are being accessed, from where, and by whom
- Ability to create multiple IT admin accounts that leverage admin permissions from the IdP, eliminating the security risk of one static IT account
- Admins can enforce password policies via the identity provider, maintaining consistency and security across all users
Password Sync
- Jamf Connect forces a user to have the same cloud IdP and Mac account credentials, and keeps those credentials in sync by leveraging a single identity for everything needed to be productive (with the exception of Google Cloud Identity)
If the cloud identity provider supports SSO Extensions on the Mac, admins will be able to monitor when a user has accessed a protected resource or service from their device, providing a way to audit access and information, but not for the device they access the info/resource from. However, while Jamf Connect supports several cloud identity providers (Okta, Microsoft Azure AD, Google Cloud Identity, IBM Cloud, OneLogin and PingFederate) today, the new SSO Extension framework is dependent on cloud identity providers, who have not yet communicated their timelines for support.
With Jamf Connect, an end user unboxes their Mac, powers it on and leverages a single corporate identity to gain immediate access to the resources they need to be productive. Users will have an improved and secure experience on any Mac, while admins gain the confidence that security and compliance measures are met all with a more organized, easy-to-manage Mac fleet.
We've created a simple infographic to further explain the differences of macOS Catalina and Jamf Connect. And when you're ready, request a trial of Jamf Connect and put these security workflows to the test.
by Category:
Have market trends, Apple updates and Jamf news delivered directly to your inbox.
To learn more about how we collect, use, disclose, transfer, and store your information, please visit our Privacy Policy.