trust
/trəst/
noun
- firm belief in the reliability, truth, ability, or strength of someone or something.
"relations have to be built on trust" - an arrangement whereby a person (a trustee) holds property as its nominal owner for the good of one or more beneficiaries.
"a trust was set up"
The definition of trust above, as maintained by Oxford Languages, provides for two distinct meanings of the commonly used word. While the second pertains to legal matters, the first provides a clear-cut explanation relating to the “reliability, truth, ability, or strength of someone or something.”
But trust goes beyond this simple definition. In fact, there are various forms of trust. Specifically, the following two are the most common:
- Particularized: Trust in people specifically known to the individual also referred to as “knowledge-based trust”.
- Generalized: Trust that people have in the members of society in general. Think of it like, “blind faith”.
You may be thinking, I thought I came to Jamf’s website for IT and Security information – not an English lesson? And you’re partially right in that thought except that there’s a “trust” connection between IT and users, securing devices and data against bad actors, as well as safely accessing corporate information from devices and within the apps or services we use, well, get work done.
Organizations need to be able to trust employees to be productive, to work from anywhere and to do so from the devices they feel most comfortable with to do their absolute best, right? But that must all be balanced against the very real-world(and sadly growing) need to keep devices, users and sensitive data – including user privacy information – protected and secured against risks and threats from those that seek to compromise any or all of the above for their own nefarious means.
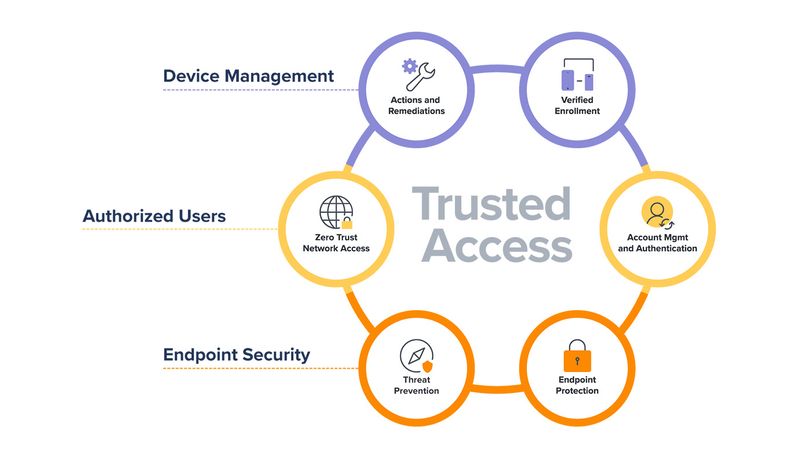
Enter Trusted Access.
The end-to-end solution from Jamf, the industry leader in best-of-breed, Apple-first solutions that integrates device management, identity provisioning, secure connectivity and endpoint security into one comprehensive, holistic and centralized platform.
Three security paradigms – one platform
Trusted Access in an unsecure world leveraging workflows that take aim at not just protecting the device, but also the user and the network to combat a variety of risks and a growing number of threats with enhanced security measures that work together to:
- Maximize layered security protections/defense in depth
- Monitor systems processes and prevent malware threats
- Keep endpoints and apps up to date with patches
- Maintain compliance through context-aware policies
- Provision cloud-based identities and centralize password management
- Secure remote connections with next-generation ZTNA technology
- Analyze endpoint health frequently to mitigate baseline shifts
- Ensure optimal performance without compromising security or privacy
- Obtain rich telemetry data to inform IT and Security team decisions
- Remediate security threats while reducing risk
Management
The crucial foundation of Trusted Access. Managing devices begins before ever receiving the device from Apple or your preferred reseller. With deep integration with Apple Business Manager, Jamf and Apple form a critical bond that shepherds devices securely through automated enrollment into Jamf’s mobile device management (MDM) solution – Jamf Pro.
But wait, what if you rely on personally-owned devices or have a mix of company- and personally owned devices to manage? All ownership models are welcomed in Trusted Access because Jamf knows that every organization’s needs are unique and will vary, so we’ve embraced both forms of enrollment:
- Device-based: Automated enrollment process for company-owned devices for fully managed environments.
- User-based: Enrollment process for personally owned devices, leveraging Trusted Access to authenticate users prior to enrolling their devices, securing devices and company-data access without infringing on user privacy or impacting personal data.
Both provide organizations and users alike the flexibility to rely on the devices that meet their needs while offering a seamless and secure way to manage Apple devices and how they access corporate data, continuing to provide an excellent Apple user experience while upholding user privacy.
After enrollment is completed, Jamf’s centralized console is where you deploy secure baselines to configure your devices, set up and configure applications for installation on managed devices and perform the crux of your management tasks using the array of remote commands – all based strictly on Apple’s security framework.
Identity
It's great to enforce passwords, but isn’t it better to integrate your identity requirements by supporting all major cloud-based identity providers (IdP), like Okta, Microsoft and Google for centralized account and password management?
Doing so with Jamf Connect as part of Trusted Access permits organizations to extend their existing IdP solution to the Apple endpoints without having to invest in new infrastructure or migrate to a new platform. By simplifying integration, permits organizations to reap the benefits of developing and maintaining consistent password policies across their entire fleet and enable cloud logging of authentication requests while implementing role-based access control (RBAC) for centralizing and securing permissions management in accordance with industry best practices, such as least privilege.
Additionally, requiring multifactor authentication (MFA) gives all stakeholders the added assurance that both business apps and sensitive data are protected via an additional layer of security before access is granted to users. Also, Zero Trust Network Access (ZTNA) – part of Jamf Connect – is the next-generation technology that bridges connectivity and security to seamlessly enable users to access all of their clouds (private, public and SaaS), alongside on-premises resources while gaining access to only what they need to perform their work functions and based on their verified identity and device.
Security
Rounding out the trifecta is everyone’s favorite topic: security. Did you know that Jamf Protect actively protects macOS and mobile device endpoints while monitoring for threats? Trusted Access does this and so much more! Not only does our solution evaluate your verified devices for health, risk and compliance statuses, but by doing so, we can signal changes in real-time that report findings to logs in addition to sending real-time alerts to security administrators for triage and/or remediation.
In fact, it performs all these tasks while also detecting known and potentially unknown threats, including stopping zero-day phishing attacks (though more on that in a bit). Indeed, Jamf Protect offers behavioral analytics too that can be adjusted to address your risk appetite or even create custom analytics that give your IT and security teams granular control over threat hunting to detect issues before they lead to compromise or data breach. For mobile devices, like iOS/iPadOS, Jamf Protect offers context-aware policies that actively check for device health, determining if endpoints have been compromised or merely lack required patch levels, automatically performing actions to remediate issues detected.
And then there’s MI:RIAM, the advanced machine learning (ML) and threat intelligence engine that drives the identification and prevention of novel threats, on-device and in-network – across all supported device types regardless of ownership model.
“122,000 zero-day phishing attacks stopped in the last twelve months”
Lastly, speaking of threat hunting, Jamf has its own team of dedicated, seasoned security researchers and Apple experts – the Jamf Threat Labs team. They work tirelessly to track the latest threats affecting macOS and iOS/iPadOS – both unknown ones waiting in the wings to stealthily compromise your Apple fleet and known threats that are constantly evolving their tactics to gain unauthorized access to your organization’s sensitive data, exploit critical systems and compromise user privacy any chance they get. With an established history of identifying some of the most novel security threats affecting macOS and iOS recently, we have deep expertise in monitoring for, detecting, remediating and ultimately protecting against the most sophisticated attacks affecting Mac and mobile devices.
Oh yeah, and for remote and hybrid workers needing to establish secure connections over untrusted networks like from public Wi-Fi hotspots, Jamf Connect’s ZTNA technology also goes several steps beyond legacy VPN by automatically securing connections without relying on users to enable them. In fact, the advanced microtunnels used by ZTNA create a unique tunnel for each app or service requested, segmenting access so that if an app or service were to become compromised, only the affected app/service need be disabled until IT/security teams have been able to resolve the issue. This permits users to continue confidently and securely working with unaffected apps/services without interruption nor impact to productivity.
Five against one
With Apple-specific threats continuing an upward trend, the sheer types of threats and attacks in the wild vary in aim and scope. Furthermore, the collateral damage caused by bad actors exploiting vulnerabilities in apps and system software scales exponentially when multiplied by the number of endpoints used to access and interact with organizational data.
A little help would be nice, wouldn’t it? It sure is! And that’s exactly what you get with Jamf. More specifically, for each threat that attempts to target a device, user and/or your critical data, you get five – count ‘em – five powerful services that work in tandem to:
- Manage your entire device fleet: from deployment to configuration to apps and patches
- Integrate and extend authentication and permissions workflows
- Monitor endpoint health while preventing malware through updated analytics
- Aid in maintaining compliance and integrate with risk-aware policies to automatically remediate device health issues detected
- Secure remote access connections leveraging advanced ML to adapt to modern computing requirements, extending on-device and network protections across your entire fleet
Each of these solutions is designed by Jamf for Apple (not open-source technologies that are merely rebranded). No, our solutions are developed in-house to help organizations of all sizes and spanning all industries to deploy, manage, secure and maintain all their endpoints with support for all devices in the Apple ecosystem and made possible under one platform. That’s Jamf Trusted Access – often imitated, but never replicated.
Let’s take a moment to meet each of the solutions that make up an integral component of the Trusted Access solution and learn how they uphold the end-user experience and keep users productive while protecting endpoints and maintaining compliance.
Jamf Pro
All the management capabilities you need in one package. Bow included.
Our flagship MDM solution and the premiere Apple device management tool empower IT pros as well as the users they support. Jamf Pro delivers on its promise of a platform that unifies managed of the entire Apple ecosystem with no compromises or caveats.
Beginning with Zero-Touch deployment of your company-owned or BYO devices, Jamf Pro’s ability to manage the day-to-day tasks includes configuration profile management, app deployment integrated with Apple’s App Stores to install managed apps while ensuring that they remain up to date across your entire fleet. Have a custom app or critical third-party app that isn’t part of the app store? No worries! Let Jamf’s App Installers (part of our App Catalog) perform the heavy lifting for you. Whether you need to automatically install complex software suites, like Adobe CC, or want to configure a simpler way to keep managed apps on your devices patched – Jamf Pro helps IT do more with greater features to simplify App Lifecycle Management.
Among the incredibly useful features, is our solution’s ability to provide IT a wealth of current inventory data at the mere tap of a screen, but the cloud-based service ensures that this information is accessible from anywhere, at any time and as secure as the devices being managed.
Jamf Connect
Simplify the user experience…while eliminating support challenges for IT.
Imagine your users being able to get on-boarded with their new Mac in a simple, three-step workflow:
- Users unbox their Mac.
- Power it on.
- That’s it – no step three!
Moreover, no tickets to set up their new Mac, manually install needed apps unique to their work experience or tediously configure the device, macOS and security and privacy settings. In fact, IT isn’t required to lay a finger on the new device, have it brought into the corporate office or any other such manual intervention. The user’s new Mac is shipped directly to them, wherever they may be, to take care of the unboxing meanwhile the apps, settings, configurations, permissions and patches that are maintained securely within the MDM are pushed down to the device after the user has successfully logged on with their cloud-based account.
This triggers the kick-off of the initial setup process that occurs automatically (and in the background, if you wish) without necessitating any further input or feedback from the user. The end result is that users are able to get online and be more productive sooner – rather than later.
Thanks to its tight-knit integration with your existing IdP, Jamf Connect not only provisions account access but extends additional security processes, such as password management and synchronization, enables Single Sign-On (SSO) for accessing managed services and apps quickly and securely and without having to enter your password a dozen or so times and implements MFA to further secure access to protected resources by confirming that users are who they claim to before access is granted.
Still not impressed? How about if we told you that the best, strongest password policy included requires no password? Allow us to explain. Passwords, even complex lengthy ones are subject to being exposed by security breaches, social engineering attacks, like phishing and unintentionally exposed by users themselves (we’re looking at you with the password written on a note stuck to the bottom of your keyboard. You didn’t think that was really fooling anyone, did you?)
So, it should come as no surprise that the best password is not the longest, most complex or hardest to guess. Rather, it’s the one that doesn’t rely on any random combination of characters or symbols to keep your precious data safe. Enter Jamf Unlock, the solution that allows users to unlock their Mac with only their mobile device – without using a password. Better still, Jamf Unlock is included as a component of Jamf Connect and by extension, Trusted Access to keep device and data access managed securely.
Oh, and since it relies on modern authentication standards, it frees your organization from maintaining on-premises Active Directory services – say goodbye to your regularly scheduled binding-related headaches – you’re welcome.
Jamf Protect
Gain insight and stop attacks before they strike.
Which would you prefer: endpoint protection that is purpose-built for macOS and aligns with existing Apple security to prevent malware threats or one that is little more than a bolt-on piece of software that may not completely defend against attacks?
The choice is simple: Jamf Protect for macOS amplifies Apple’s core security features with:
- Stronger controls
- Better preventions
- Broader visibility
- Automated remediations
- Expanded integrations
- Unparalleled support
- Enforced baselines
- Regulation compliance
- Real-time alerting
- Powerful API
Comprehensive insight into Mac-specific malware and threats is the key to identifying, preventing and remediating known risks, such as malware, spyware and the ever-dreaded ransomware from gaining a foothold into your endpoints. Combined with behavioral analytics that is mapped to the powerful MITRE ATT&CK Framework easily identifies suspicious and malicious activity. Plus, allowing for full customization means analytics can be easily adapted to your unique environment, adding the threat-hunting capability to your security team’s roster of skills to proactively hunt for threats that stealthily and specifically target your environment.
“Maintaining the peace” helps to minimize risk through strong, policy-based security management that blends real-time visibility with compliance policies aligned with CIS benchmarking standards out of the box. Additionally, Jamf Protect High Compliance – an included component of Jamf Protect – contains all the tools necessary for organizations to capture and analyze audit data across your Mac fleet to minimize non-compliance through real-time identification and automated remediation workflows driven by the integration between Jamf Pro and Jamf Protect.
And many more capabilities are made possible through access to the Jamf API, such as the ability to introduce complex scripts, as well as extending features through unprecedented integration with first- and third-party security apps, including Jamf Connect for IdP, centralized logging and reporting through your preferred SIEM solution and visualizing endpoint health data through customized dashboards, like those made possible with Splunk to name but a few of the growing possibilities.
Mobile threat defense…and the power of the platform.
Apple’s increased enterprise adoption coupled with the rapid growth surrounding the platform’s popularity among consumer users makes for an increasingly appealing target for bad actors. Mix in remote and hybrid work environments with users’ expectations of taking their work – and play – on the go, and the need for a holistic endpoint security solution focusing on protecting mobile devices while minimally impacting the user experience becomes a requirement of modern-day computing.
Like the macOS-specific endpoint protection above, Jamf Protect protects mobile endpoints running iOS/iPadOS from being compromised by detecting, preventing and remediating against Apple-specific threats that exist on-device and in-network, like malware or zero-day phishing attacks.
Through multi-prong defense capabilities, Jamf’s mobile threat defense solution leverages the following modern technologies to stop threats cold and minimize risk to your mobile fleet:
- Advanced machine learning (ML) provides threat intelligence and prevents novel threats
- In-network protection blocks zero-day threats, like phishing attacks, malicious domains and Man-in-the-Middle (MitM) attacks
- Device health insight provides IT and security teams with real-time insight into risks while automated policies mitigate identified threats
- Unrivaled integrations maximize your investment in Trusted Access by leveraging Jamf’s Risk API to extend capabilities securely across your entire mobile fleet
- Safeguarding privacy is important to users and Jamf upholds this with strong encryption to protect personal data and ensure regulatory compliance
- All modern mobile devices are supported – regardless of if they are personally or company-owned
- Jamf Trust app that centralizes and extends security protections from Jamf Protect and Jamf Connect for macOS, iOS/iPadOS, Android and Windows
Meet MI:RIAM – short for, “Machine Intelligence: Real-time Insights and Analytics Machine” – the ML technology that drives Jamf Protect. MI:RIAM can perform tasks at speeds that manual intervention by humans simply cannot keep up with. A few examples of how ML supercharges your endpoint protection and threat-hunting efforts while minimizing risk from mobile threats are:
- Identify additional attack types, like cryptojacking and command & control (C2)
- In-network protections for apps and services, including web browsers, email, social media and SMS
- Assess device health through frequent checks to identify and remediate vulnerable configurations and risky connections
- Obtain detailed threat intelligence reports with app insights, permissions and embedded URLs
- Enforcement of security policies in real-time to minimize risk across the fleet while integrated alongside first- and third-party tools
- Continuous monitoring of rich telemetry data and conceptual input sets informs adaptive access to apps and services by trusted devices
Jamf Connect
Keep users protected – and productive with Zero Trust Network Access (ZTNA).
The network perimeter is gone. The days of being safe when working from behind the company’s firewall are no longer valid when users are working from remote locations, like their homes, shared-work spaces, coffee shops or from 30,000 feet above – all connected to public, free Wi-Fi.
The rise of remote and hybrid work environments, coupled with a mix of mobile devices – some issued by your company, while others personally owned by employees – but all connecting to sensitive organizational resources require a new way of ensuring that data is accessed securely while maintaining the confidentiality and integrity of your data regardless of the ownership model or device type being used to request access.
This is where Jamf Connect's ZTNA capability shines by ensuring that only authorized users on compliant devices are able to access protected resources – all others are denied.
Welcome to ZTNA, the advanced solution that blends secure remote access with conditional access workflows, purpose-built to take advantage of modern computing landscapes. Trusted Access resolves the challenges and limitations of legacy VPN technology by:
- Eliminating the need to deploy, manage and maintain complex hardware and software configurations associated with legacy VPN – cloud-based infrastructure supports all modern devices, operating systems and security tools
- Integrating directly with IdP to centralized account management, extending secure access to devices and organizational resources through SSO
- Streamlining permissions by granting users access to only the apps/resources they authorized for – nothing more – enforcing least privilege
- Creating unique microtunnels for each app/resource request, minimizing the risk of compromise and preventing lateral movement through intelligent network segmentation
- Enforcing risk-aware access policies that restrict access to users and devices that may be compromised or do not meet minimum established requirements for security across your entire infrastructure
- Enabling always-on security optimally and automatically in the background to ensure business connections are secured while intelligent-split tunneling routes non-business traffic directly to the internet
- Minimal resource utilization ensures fast, efficient connectivity seamlessly connects to resources securely without impacting performance or interfering with the user experience
Never trust – always verify! That is the creed of ZTNA and by extension, Trusted Access integration between Jamf solutions operates under this condition, with Mac and mobile devices checked for compliance whenever making requests to access organizational resources – whether they are hosted on-premises, public and private clouds or SaaS applications – context-aware, granular policies extend throughout your infrastructure to standardize data security from end to end.
The Power of One
One Love. One Trust. One Powerful Platform.
This is the difference that Trusted Access provides. You. Your organization. Your users. Your endpoints. And your data – all protected, comprehensively and holistically from end to end under one powerful, yet easy-to-manage platform that integrates five solutions into the ultimate Apple device and endpoint management solution.
One that fully encompasses the desktop, application management and security lifecycles seamlessly to provide all organizations of any size with all the tools necessary to succeed with Apple at work.
Key Takeaways:
- Solutions work in conjunction, providing comprehensive, holistic support for your entire Apple fleet throughout the entire desktop, application and security lifecycles.
- Centralize management of devices, identity and security.
- Develop customized workflows, enabling automation that is tailored to meet your organization’s unique needs, while keeping your devices, users and data security and user privacy safe.
- Maintain compliance by aligning regulatory requirements with organizational policies to easily audit endpoints and verify compliance goals are met or dispatch remediations to bring endpoints back into compliance
- Real-time alerts and reports identify potential issues while behavioral analytics and advanced machine learning prevent threats and mitigate risk
- Purpose-built, Apple-first solutions that align with Apple native tooling and frameworks, not only maintaining the user’s experience but working seamlessly in the background to keep endpoints performing optimally and securely
- Empower employees to manage their devices securely through Self Service while providing them the agency to focus on productivity without waiting on answers from IT
- Manage devices and endpoint health efficiently and effectively without having to rely on juggling multiple incompatible tools to cobble together workarounds
- Implement defense-in-depth strategies that harden device configurations, employ patch management, integrate identity-centric authentication, secure remote connections, establish context-aware, policy-based management of access and permissions while provisioning best-of-breed endpoint security protections across your entire Apple fleet
- Integrate solutions to develop automated workflows, extend capabilities and support for all Mac and mobile devices to fully address security challenges to the modern computing landscape
Better still, see Trusted Access in action for yourself!
Contact Jamf or your preferred reseller today to get started with your trial.
Subscribe to the Jamf Blog
Have market trends, Apple updates and Jamf news delivered directly to your inbox.
To learn more about how we collect, use, disclose, transfer, and store your information, please visit our Privacy Policy.