Are you ready to step up your Apple Mobile Device Management (MDM) and looking for practical, reliable training to securely manage your fleet of Apple devices?
Do you want to ensure that all security protocols are in place across all areas of the digital environment, including and especially iOS and iPadOS?
Check out The Advanced Guide to iOS/iPad OS Management, Jamf’s 201-level e-book followup to our iPhone and iPad Management for Beginner’s e-book.
Read on for highlights of what you can learn from this new resource.
Modern cybersecurity for a mobile workforce
As more workplaces have enabled remote and hybrid work, the cybersecurity landscape has changed. Traditional firewall-based security and management systems simply were not built with mobile devices in mind, and don’t provide the best protection or experience.
The most critical challenge facing InfoSec and IT admins managing today’s mobile workforce: how to keep workplace devices and data secure while enabling workers to be connected and productive on every device, no matter where they work.
So how can your organization mitigate emerging cyber risks, while still providing the best user experience?
Build the foundation of security for your Apple fleet on proper management.
While it’s not the full picture of the security landscape, secure management is only possible when proper iOS management/iPadOS management is in place.
When developing your management plan, it’s vital to consider the key capabilities, workflows and settings needed to securely manage your iOS and iPad OS fleet.
Encryption, parameters, compliance and more
Moving beyond basic MDM requires a good understanding of Apple mobile device security features and important management tools, settings and workflows.
Read our new guide for detail about important security features including:
- PKI certificates – encrypted text files with identification data on users and devices to secure all communications.
- Push certificates - encrypted files generated by Apple that establish trust between a third-party service like Jamf Pro and Apple Push Notification Service (APNs).
- Conditional access – setting parameters for securing an organization’s data in multiple locations; access requires verification of both trusted device and trusted user.
- Device compliance – enforcing policies that may not only be required by an organization, but also by industry or government mandates, via a thorough and well-crafted device compliance management program to keep devices, users and data secure.
- Configuration profiles – MDM commands and settings available to admins to secure control; configuration profiles can enforce and enhance security in their own right by enforcing security protocols in passcodes, behavior and more.
Key workflows discussed include:
- App management – from sourcing and hosting to updating and deploying, proper app management is critical in securing an Apple fleet while also supporting end-user productivity.
- Bring Your Own Device (BYOD) – combining profile- or account-driven user enrollment with Jamf mobile device management means that you can secure and manage any employee-owned device.
- Mass actions – Perform multiple tedious tasks on many devices simultaneously.
Jamf security solutions for iOS and iPadOS
While proper device management is vital to proper security, using security-specific tools on top of that foundation is essential to create a comprehensive security solution. Read Mobile Threat Defense for Beginners for a basic overview.
Jamf security solutions for threat defense and endpoint protection go beyond simple antivirus for malware, including:
- Identity and access management
- Threat prevention and remediation
- Content filtering and safe internet
- Zero Trust Network Access (ZTNA)
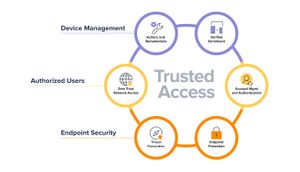
Trusted Access is Jamf’s solution for security beyond management, a unique workflow that brings together device management, authorized users and endpoint security to help organizations create a work experience that users love and a secure workplace that organizations trust.
Download The Advanced Guide to iOS/iPadOS Management.
by Category:
Have market trends, Apple updates and Jamf news delivered directly to your inbox.
To learn more about how we collect, use, disclose, transfer, and store your information, please visit our Privacy Policy.